Cezurity has always focused on creating innovative technologies that protect computers and user information.
There was a time when the anti-virus industry needed to protect users from only one main type of threat: viruses. In the 1990s, anti-virus software needed only to defend against a few dozen known viruses. Security software always had “anti-virus” in the name, leaving no confusion about the features or threat the software was meant to address. Although viruses were able to harm a computer or a victim’s data, their creators rarely were able to make money from the mayhem caused.
The threat landscape changed, however. Today’s virus creators are in it not to have fun or to make a point, but to cash in. Cybercrime is the domain of professionals, who are crafting targeted attacks and creating more threats than ever before. Anti-virus protection can be neutralized or circumvented in any number of ways.
The breaking point for the anti-virus industry came in 2005 and 2006, when the amount of malicious software grew exponentially even as it became more and more complicated. In 2005, the virus database of AV-Test.org, a research laboratory that tests anti-virus software, held fewer than three million samples of malware. In 2010, this number jumped to over 40 million, and in 2012, this number exploded again to over 100 million. Traditional anti-virus solutions had fallen behind, unable to keep up with the growth in malware and vulnerable to malicious deactivation. Low-level attacks were too much to handle for the protection available at the time.
This spurred the developers of existing products to look for new solutions to keep users safe. Different companies took different paths, based on new technologies that reflected each company’s understanding of the cyberthreat landscape.
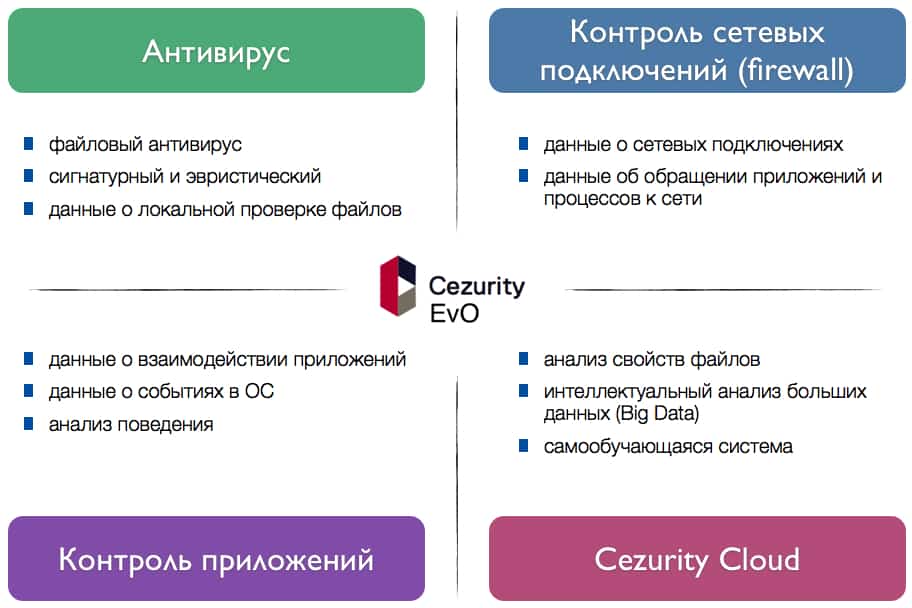
Key technologies in Cezurity solutions:

Centralized detection engine
Event chains
Context
Real-time analysis
Why Cezurity EvО is better than other detection methods:
- Minimal performance hit.
- More precise detection and more reliable protection. Fewer false positives: in most solutions, reducing false positives requires reducing the protection level (more aggressive protection causes more false positives).
- Real-time protection reduces the risk of system infection.
- The software works autonomously, requiring less intervention and decision-making by the user.
- Protection from currently unknown (zero-day) malware and attacks.
- Protection from rootkits.
- Self-defense prevents attackers from disabling anti-virus protection.
- New: protection from advanced persistent threats.
- New: monitoring of applications and full implementation of default deny capabilities (“forbid everything that is not allowed”).
- New: ultrasafe apps. This feature, a new one for anti-virus solutions, allows protecting the data inside applications and user folders.

-
Cloud-based technology for detecting malware.
In-the-cloud analysis of file properties
User computers collect a large amount of information about file properties and send it to the cloud. On our server, the data is classified and stored in a special database. Cezurity Cloud analyzes over 200 properties for each file, including the countries in which the file is most popular, where the files are found in the system, and how the files behave when run.Self-learning
As information is processed and the danger of different objects is evaluated, new classifications are generated automatically – which makes Cezurity Cloud a self-learning system that is constantly getting smarter. And if there is not enough information to be sure about the danger of an object, it asks for additional information.Smart analysis of Big Data
Cezurity Cloud uses special techniques for processing Big Data to ensure the best possible anti-virus analysis.Why it’s better:
- Precise detection
Cezurity Cloud is an effective solution for some of the most vexing problems facing the anti-virus industry today. First and foremost, this means detecting malware with greater precision, even as malware becomes more complex and more numerous. - A new approach to cloud-based anti-virus protection
Cezurity Cloud examines more object properties than do other cloud-based solutions. This opens up opportunities for use cases that go beyond reputation-based file detection or whitelisting. - Flexibility
Cezurity Cloud has the flexibility to fit into diverse solutions. Different information can be sent and processed by the server, depending on the needs of each product or solution. For example, Cezurity Cloud is currently used as a subsystem to supply data for the Cezurity EvO detection engine. Cezurity Cloud helps the Anti-Virus Scanner to detect malware. In addition, the technology is used for monitoring and analyzing changes in our APT-D solution designed to detect persistent threats against corporate networks. - Dynamic Threat Detection
Protection of corporate IT infrastructure from advanced persistent threats (APT) is the mission of Dynamic Threat Detection by Cezurity. Featured in our APT-D (Advanced Persistent Threat Detection) solution, this technology monitors systems for changes and analyzes changes that are anomalous.
Monitoring of system changes
Critical areas of memory on each of the computers in your protected IT infrastructure are periodically scanned. The scanning process collects and classifies many types of data about the state of the system. This data is compared to the results of previous scans.Search and analysis of anomalous changes
The first step of analysis identifies anomalous changes that have taken place since the previous scan. While anomalies can take place for any number of reasons, any attack attempt will cause anomalies. So during the second step, Dynamic Threat Detection analyzes the anomalies found, determines the cause for them, and classifies any attacks accordingly.Cezurity Cloud technology
Cezurity Cloud monitors for changes, acting as a smart self-learning system that looks at file properties and application behavior.Benefits and features:
- Different “calling cards” of advanced persistent threats are taken into account: duration, step-by-step execution, and necessity for the attacker to evade protection mechanisms.
Attackers take steps to avoid getting detected. So any particular aspect of the system might not look suspicious. But looking at the changes can allow spotting the attack all the same: if the IT infrastructure is attacked, this will eventually cause an abnormal change in at least one system, alerting you to what is happening. - One solution for detecting all types of attacks.
Other solutions are often piecemeal: they might be good at one type of attack but prove useless for another type. Perhaps it can spot anomalous network traffic – but it can’t correlate this event with the appearance of new files in critical areas of the operating system. Using several solutions for protection at the same time can be a hassle for administrators, which impairs the overall level of protection. - Quick detection.
Dynamic detection allows you to detect attacks right away – immediately after a critical malicious change has been found in a protected system. - Easy to deploy and get started with.
Dynamic detection is based on endpoint monitoring, so it is independent of your company’s infrastructure and network topology. Our solution is easy to deploy and get started with even if your IT infrastructure is complicated and contains diverse system types. - Low performance overhead.
The most resource-intensive analysis is handled by our cloud platform (Cezurity Cloud) – the CPU hit on your company’s computers is minimal. - Closed Secure Environment
Closed Secure Environment can protect critical infrastructure, including such SCADA and embedded systems as ATMs, payment terminals, and more.
System events monitoring by hooking system calls
Our Closed Secure Environment technology controls the events that take place in the system, thanks to low-level interception of system calls. Low-level control (as close to the metal as you can get) of network interaction is combined with bilevel cross-checking.Security policies for each action
Each action is subject to a rule or set of rules, called a security policy. This allows you to whitelist actions on critical systems – forbidding everything that is not explicitly allowed – which is considered best practice.Restricted actions
The behavior of applications and the OS inside the closed secure environment is tightly controlled. Each application can perform only the actions that are allowed for it.Access control
All system and critical processes are protected from interference by other software. Each process can be affected only in an allowed way. For example, malware cannot infect a trusted application that has broad system rights in order to perform actions under that application’s cover.Benefits and features:
- Ultra-high reliability
Closed secure environments are one of the most foolproof ways to ensure the safety of SCADA systems and critical infrastructure. Our technology completely isolates the processes running on the computer from the effects of any other software. - Monitoring of all critical events
Our technology allows implementing a “white list” of actions, which forbids all actions that are not explicitly allowed. Any forbidden actions can be blocked automatically or remotely, via centralized system management. Application actions in the system are monitored and supervised, such as hidden creation of files, hidden program launch, interaction with other processes (injection of malicious code), network access, etc.
Cezurity Closed Secure Environment technology prevents even processes that the OS can’t see from sending or receiving data. Even zero-day rootkits with their own kernel-level TCP/IP stacks can’t get through! Our technology also allows using patterns found in logs of application interactions to detect attacks. - Flexibility
Cezurity solutions can be configured for client-specific needs. For example, the number of events that are analyzed can be increased. Data analysis logic and decision-making can be set individually for each type of event, depending on whether you want to forbid, allow, or log the action.
- Ultra-high reliability
- Different “calling cards” of advanced persistent threats are taken into account: duration, step-by-step execution, and necessity for the attacker to evade protection mechanisms.
- Precise detection